How to run application blocked by Java security
In this article, we will show you why java security blocks the application.Java is a ubiquitously used programming language. Java team is constantly improving the language’s security features. It is quite common to see Java security warnings while running some programs. This is not like a regular security warning prompted by the operating system.
In this article, I am trying to provide an overview of how to work with Java security settings and what to do when an application is blocked by the Java security system.
1. When does Java security block the application?
Java 7 introduced an ability to manage when and how an untrusted Java application can be run. The moment Java Security system sees an application as a potential risk, the system stops it from running. Some typical scenarios are as follows,
1.1. Unsigned Application
Any application not signed by a trusted certificate authority is blocked by Java. Even the missing name or missing publisher information will attribute to blocking the application. It is potentially very unsafe to run this kind of application.
1.2. Self-signed applications
Application not signed by the authorized certificate authority is very risky to run and they are blocked by default. Own signatures can’t be trusted and they are hindered from getting the file system access.
1.3. Permission attributes missing in the bundle
Normally Java applications are bundled as jar files. Each application must contain the permission file that specifies the privileges required to run the application. If this file is missing, attackers can mimic the same applications with their permission files and easily get access to our computer.
Normally, applications exhibiting the above characteristics are blocked by Java as they don’t meet Java’s security guidelines. In such cases, it is advised to contact the developer or the publisher of the application.
2. Java security explained
Java Security model is focused on protecting the user’s machines from hostile programs.Java accomplishes it by providing a customized sandbox environment to run the untrusted code and application. These Java applications can run only in the boundaries of the Java Sandbox. Sandbox protects us from hostile activities like,
- Unauthorized file access (reading and writing to the file system)
- Making network connections
- Calling native methods and invoking new processes
- Downloading code
In the traditional security mode users were responsible for scanning the application using antiviruses to ensure safety. With Java sandbox, users can try to run any application and Sandbo will take care of giving permissions and verifying the authenticity of applications.
The Java sandbox is completely customizable. You can customize the sandbox by implementing your own class loader and SecurityManager.
Some of the Java Virtual Machine’s safety features are as follows,
- Byte code verification before running
- Tape safety
- No support for pointers
- Automated garbage collection
- Array bounds checking
- Null reference checking
More reading on Java security can be found here.
Note that from Java 8, applications signed using MD5WithRSA and MD5WithDSA are blocked.
3. How to run a blocked application?
In this section we will see how an application blocked by Java Security can be run.
Java 7 introduced an ability to manage when and how an untrusted application can be run. The various security level decides whether unsupported applications are totally blocked or the user is asked for permission to run.
This section applies to the Windows platform and Java version 8 or higher.
To access Java control panel in Windows, follow the below steps,
- Go to Control Panel
- Click on Programs
- Click on Java to launch Java Control Panel
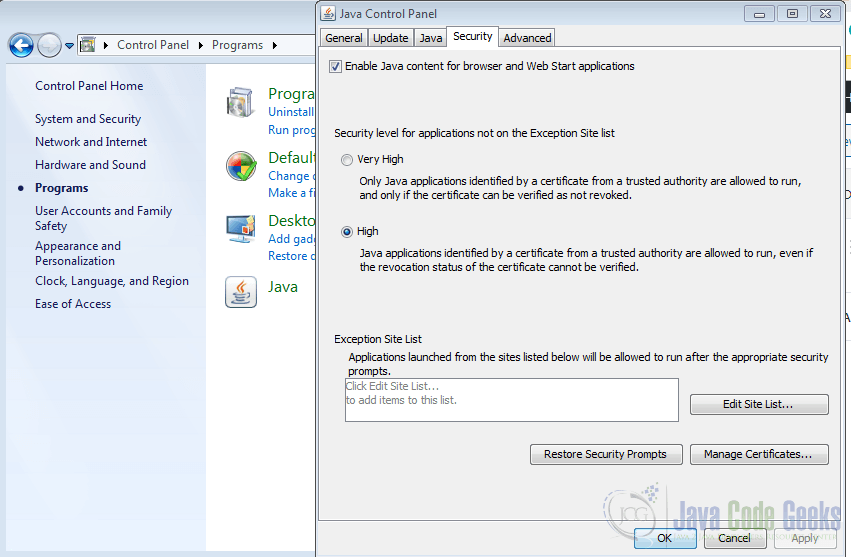
- Go to Security tab to change the security settings
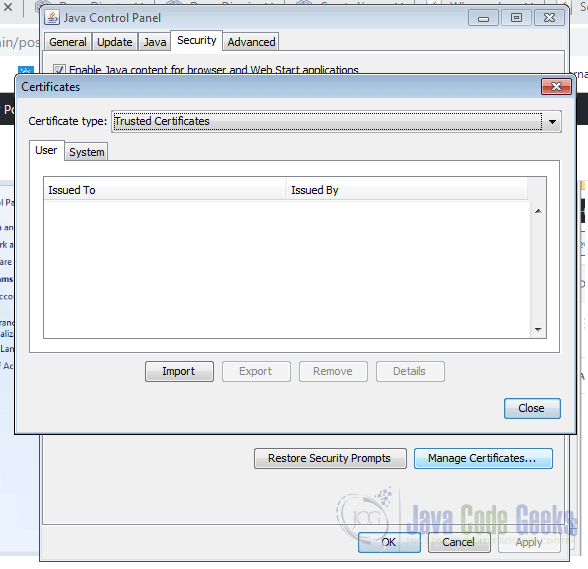
Trusted certificates are listed under the Manage Certificates tab. Also, a trusted certificate can be added here.
By changing the security level and adding certificates we can run the blocked trusted applications in Java.
3.1. Java security levels
In this section let us see each of the Java security levels.
3.1.1. Very High
This is the most restrictive security level. Only the applications with a valid certificate and permission attributes in manifest file are allowed to run after the prompt, all other applications are blocked.
3.1.2. High
This is the default recommended security setting. Applications with a valid or expired certificate and that include permission attributes are allowed t run with a security prompt. Even though certificate revocation status can’t be verified, the application can be run. All other applications are blocked.
3.1.3 Medium (Removed from Java 8)
Only unsigned applications requesting all permissions are blocked. All other applications are allowed to run. The medium-security level is not recommended as it may allow malicious applications to run.
4. Conclusion
Java takes all the due care to block the potential hostile applications. All developers need to take the utmost care to follow secure coding principles and sign their applications with valid trusted certificates.


