Amazon EC2 Security Groups Tutorial
Welcome readers, in this tutorial, we will see an introduction to AWS and the Amazon EC2 security groups.
1. Introduction
AWS represents the Amazon Web Services and it provides different services ranging from IaaS (Infrastructure as a Service), PaaS (Platform as a Service), or SaaS (Packaged software as a Service).
- It offers flexibility by giving the users flexibility of what to do and what not
- Cost-effective solutions
- Scalability/Elasticity techniques to automatically scale up/down the application infrastructure when demand increases or decreases respectively
- Provides end-to-end security configuration and privacy to its customers
- A virtual infrastructure that offers complete privacy and isolation of operations
1.1 AWS EC2
- EC2 is known as the Elastic Compute cloud which is a web service that provides resizable computing capacity in the cloud
- It eliminates the need to invest in the hardware upfront and we only pay for the resources that we use
- It is available under different purchasing options i.e. On-Demand, Reserved, and Spot instances as per the business requirement. One can refer to the following documentation available at this link for a complete overview to purchasing options
- EC2 is also available under different type variations i.e.:
- Family: Based on what they are optimized to do
- Type: Sub-category of each family type i.e. t2.micro, t2.small, or t2.nano
- Virtual CPU(s): Number of virtual central processing units the instance uses
- Memory (GIB): Amount of RAM the instance type uses
- Instance Storage (GB): Local instance storage volume (i.e. the hard drive). E.g.: Elastic block storage (EBS) or SSD
- EBS optimized available: Indicates if EBS optimized is an option for the instance type
- Network performance: Rating based on its data transfer rate (i.e. the bandwidth capacity)
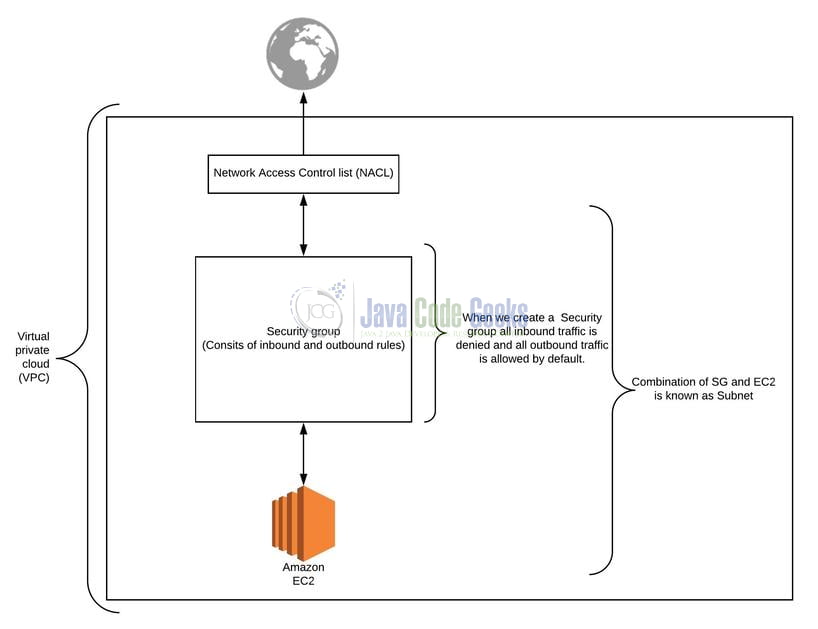
1.2 AWS Security Groups
- Security Groups in AWS stands as a virtual firewall that helps to control the traffic running into or out of your EC2 instances
- When we start an EC2 instance we associate it with 1 or more security groups
- A security group acts as the first line of defense against the hackers as we define the inbound and outbound traffic rules in a security group
- Security group are proposed on the instance as opposed to Network Access Control Access List which is proposed at the subnet level
- Security groups are stateful meaning any traffic allowed to enter into the Security group is automatically allowed to return to its source event if there is not a matching outbound rule in that Security group
1.2.1 Security Groups best practices
The following points list down some of the common security groups practices that one should follow:
- As the Security groups are not numbers, one should use the proper naming conventions for them. For instance – AWS Region + Environment Code + Operating System Type + Application Tier Level Code + Application Code
- Attach policies to Security groups rather than individuals
- Never open ports for the entire world (i.e. 0.0.0.0/0), unless you want to set up a trap door to hack the server(s)
- Grant access from the particular IP address for any Security group
- Create a default Security group for new EC2 instances and restrict the Security groups access to prevent DDoS or Brute force attacks
- Use IAM to control permissions for creating and managing the Security groups, Network Access Control List (NACLs)
- Never allow internet access for Security groups created for the databases
- Periodically audit the security groups for optimization
- And so on. . . .
1.2.2 Different between Security Group and NACL
| Security Group (SG) | Network Access Control List (NACL) |
| Only supports the allow rules and by default, all the rules are denied | Supports both allow and deny rules |
| Stateful in nature i.e. any traffic allowed to enter the SG is automatically allowed to return to its source | Stateless meaning any change in the inbound rules will not be automatically reflected in the outbound rule |
| Associated with EC2 instances | Associated with Subnets |
| SG are not numbered and are evaluated before-hand to decide whether to allow traffic or not | NCAL are numbered and are evaluated in order (i.e. lowest to the highest number) |
| The primary layer of defense | A secondary layer of defense |
Now, let me open the AWS environment and take you through a Security Group. I am hoping that readers at this point have some prior information about the EC2 instance and how to create one. If not, they can refer to the video tutorial available at this link.
2. Amazon EC2 Security Groups Tutorial
As the initial steps readers need to login to the AWS portal. Navigate to the EC2 dashboard and then the Security groups dashboard. Once done they will land on the Security groups dashboard as shown in the below image.
Note: Some information is hidden for security reasons.
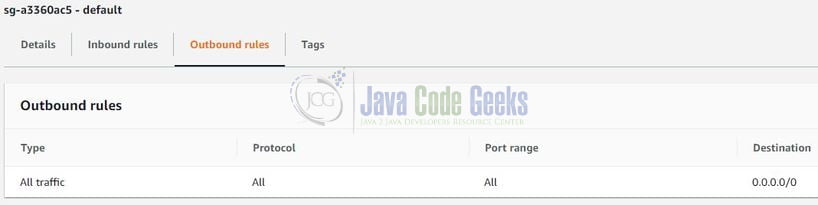
Security groups consist of inbound, outbound rules. The following image shows how the rules look like.
Once done, developers have options to edit or delete the inbound or the outbound rule. Developers need to click on the “Edit” button the rule. On the edit screen, they have an option to either define new rules or delete an existing one.
And voila, we are doing editing a rule. Always remember when we add an inbound rule, then it automatically gets added to the outbound rule. That is all for this tutorial and I hope the article served you whatever you were looking for. Happy Learning and do not forget to share!
3. Summary
In this article, we learned the following:
- We made an introduction to AWS and the Amazon EC2 Security Groups
- Difference between Security Groups (SG) and Network Access Control List (NACLs)
- Walkthrough on AWS Security Groups


