Verify if a Certificate is Self-Signed or CA-Signed
In the realm of secure communication in Java, we frequently encounter the need to verify the authenticity of digital certificates. Whether it’s for ensuring the security of data transmission or validating the identity of communication partners, the ability to check whether a certificate is self-signed or CA-signed is paramount. Java provides tools for comprehensive Java check certificate sign operation. In this article, we will explore how to check whether a certificate is self-signed or signed by a certificate authority (CA) using Java.
1. Understanding Certificate Signatures
1.1 What are Digital Certificates?
Digital certificates are electronic documents that authenticate the identity of parties involved in online transactions. They serve as a digital counterpart to traditional identification documents.
There are two primary types of certificates – Self-Signed and CA-Signed. Both of these certificates serve distinct purposes in the authentication landscape.
1.2 Understanding the Distinction: Self-Signed vs. CA-Signed Certificates
1.2.1 Self-Signed Certificates
A certificate that is signed by the entity it belongs to. There is no involvement of a Certificate Authority (CA) in the signing process and it’s typically used for internal purposes. Some use cases and considerations when using self-signed certificates are:
- They are commonly employed in private networks, for testing purposes, or in development environments.
- The simplicity and ease of issuance make them suitable for specific applications. There is the benefit of quick issuance without relying on external entities.
- The Lack of third-party verification may lead to trust issues in public-facing scenarios.
1.2.2 (Certificate Authority) CA-Signed Certificates
A certificate that is signed by a trusted and reliable Certificate Authority, creating a trust chain. It involves a rigorous verification process to confirm the certificate holder’s identity and is widely used for securing websites, applications, and other online services. Some use cases and considerations when using CA-Signed certificates are:
- CA-Signed certificates are essential for public-facing websites to instill trust among users.
- Their Inclusion in browsers and operating systems’ trust stores ensures widespread recognition. They are widely recognized and are suitable for e-commerce and sensitive transactions.
- CA-Signed certificates provide a robust security layer through the involvement of reputable Certificate Authorities (CAs). There is cost and complexity associated with the verification process.
For the rest of this article, we’ll explore how to determine if a certificate is self-signed or CA-signed using Java.
2. Checking for Self-Signed Certificates
To check if a certificate is self-signed, we first need to generate a Self-Signed Certificate that will be used in this article. We can use the keytool tool to generate a self-signed certificate or use Java’s built-in classes along with Bouncy Castle.
2.1 Run the Keytool Command
Use the following command to generate a self-signed certificate using keytool like this:
keytool -genkeypair -keyalg RSA -keysize 2048 -alias jcg -keystore keystore.jks -validity 365 -storepass your_password
When we run the above command, we’ll be prompted to provide information for the keystore, such as the name, organization, and location. We need to answer the prompts accordingly.
-genkeypair: Generates a key pair (public and private keys).-keyalg RSA: Specifies the key algorithm to RSA in this case.-keysize 2048: Specifies the key size. 2048 bits are used in this example.-alias jcg: Specifies an alias for the key pair.-keystore keystore.jks: Specifies the keystore file name.-validity 365: Specifies the validity period in days. 365 days in this example.-storepass your_password: Specifies the keystore password.
2.2 Generate and Verify Self-Signed Certificates in Java Using Bouncy Castle
First, let’s include the Bouncy Castle library in our Maven project by adding the following dependency to our pom.xml file:
<dependencies>
<!-- Add Bouncy Castle dependency -->
<dependency>
<groupId>org.bouncycastle</groupId>
<artifactId>bcprov-jdk15to18</artifactId>
<version>1.69</version>
</dependency>
</dependencies>
Next, generate a self-signed X.509 certificate using the Bouncy Castle cryptographic library and verify whether the certificate is self-signed using the following source code:
public class VerifyCertificate {
public static void main(String[] args) {
// Add Bouncy Castle as a security provider
Security.addProvider(new BouncyCastleProvider());
try {
// Generate a key pair
KeyPair keyPair = generateKeyPair();
// Generate a self-signed certificate
X509Certificate selfSignedCertificate = generateSelfSignedCertificate(keyPair);
// Check if the certificate is self-signed
if (isSelfSigned(selfSignedCertificate)) {
System.out.println("The certificate is Self-signed.");
} else {
System.out.println("The certificate is CA-signed.");
}
// Save the certificate to a file (optional)
saveCertificateToFile(selfSignedCertificate, "path/to/certificate.cer");
} catch (Exception e) {
e.printStackTrace();
}
}
public static boolean isSelfSigned(X509Certificate certificate) {
try {
certificate.verify(certificate.getPublicKey());
return true;
} catch (Exception e) {
return false;
}
}
// Generate a key pair using RSA algorithm
private static KeyPair generateKeyPair() throws NoSuchAlgorithmException {
KeyPairGenerator keyPairGenerator = KeyPairGenerator.getInstance("RSA");
keyPairGenerator.initialize(2048); // Key size
return keyPairGenerator.generateKeyPair();
}
// Generate a self-signed certificate
public static X509Certificate generateSelfSignedCertificate(KeyPair keyPair) throws GeneralSecurityException {
X509V3CertificateGenerator certGen = new X509V3CertificateGenerator();
certGen.setSerialNumber(BigInteger.valueOf(System.currentTimeMillis()));
certGen.setIssuerDN(new X509Principal("CN=javacodegeeks"));
certGen.setSubjectDN(new X509Principal("CN=javacodegeeks"));
certGen.setPublicKey(keyPair.getPublic());
certGen.setNotBefore(new Date(System.currentTimeMillis()));
certGen.setNotAfter(new Date(System.currentTimeMillis() + 365 * 24 * 60 * 60 * 1000)); // 1 year validity
certGen.setSignatureAlgorithm("SHA256WithRSAEncryption");
return certGen.generate(keyPair.getPrivate(), "BC");
}
// Save the certificate to a file
private static void saveCertificateToFile(X509Certificate certificate, String fileName) throws Exception {
try (FileOutputStream fos = new FileOutputStream(fileName)) {
fos.write(certificate.getEncoded());
}
}
}
Here is a breakdown of the main parts of the code:
- Adding Bouncy Castle Provider: We start by adding this line of code
Security.addProvider(new BouncyCastleProvider());which adds the Bouncy Castle cryptographic library as a security provider in the application. - Generating Key Pair:
KeyPair keyPair = generateKeyPair()– In this line, thegenerateKeyPairmethod creates an RSApublic-privatekey pair with a key size of2048 bits. - Generating Self-Signed Certificate: We use the
generateSelfSignedCertificatemethod to create a self-signed X.509 certificate using the provided key pair. It sets various certificate properties, such as issuer, subject, public key, validity period, and signature algorithm (SHA256 with RSA).
2.2.1 Verifying if the Certificate is Self-Signed
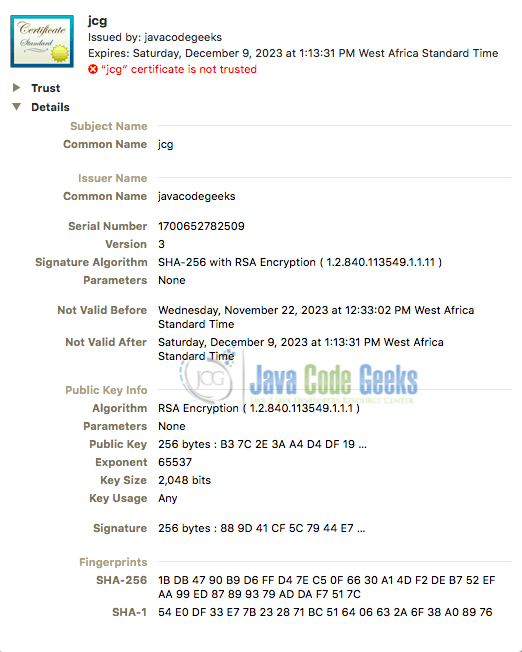
Certificates that are self-signed are certificates where the issuer and subject represent the same entity. In other words, a self-signed certificate will have identical subject and issuer fields. Hence, verifying if a certificate is self-signed involves inspecting and comparing the subject and issuer information to check for a match.
An alternative method for confirming the presence of a self-signed certificate is to verify it using its own public key. To achieve that in our class, we use the sample code shown here:
public static boolean isSelfSigned(X509Certificate certificate) {
try {
certificate.verify(certificate.getPublicKey());
return true;
} catch (Exception e) {
return false;
}
}
The isSelfSigned method checks if the given X.509 certificate is self-signed. It does so by attempting to verify the certificate using its own public key with this line – certificate.verify(certificate.getPublicKey()).
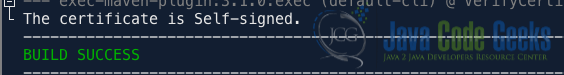
In the main class of the application, we utilize the isSelfSigned method (code snippet shown below) to determine if the generated certificate is self-signed. If the verification succeeds, the certificate is considered self-signed and prints out the following result as shown in Fig 1.0
// Code to check if the certificate is self-signed
if (isSelfSigned(selfSignedCertificate)) {
System.out.println("The certificate is Self-signed.");
} else {
System.out.println("The certificate is CA-signed.");
}
Finally, we use the saveCertificateToFile method to save the generated certificate to a file by using a FileOutputStream to write the encoded form of the certificate to the specified file path. The generated self-signed certificate is shown in Fig 2.0.
3. Checking for CA-Signed Certificates
When a certificate is signed by a CA, it means the CA has verified the entity’s identity. This verification process helps users trust the information provided by the entity. To be considered CA-signed, a certificate needs to be a link within a trust chain that ultimately traces back to a recognized and trusted root CA.
3.1 Understanding Certificate Chains
A certificate chain is a series of certificates linked together, where each certificate except the root is signed by the private key of the certificate that follows it in the chain. The last certificate in the chain is known as the root certificate, typically the Certificate Authority (CA).
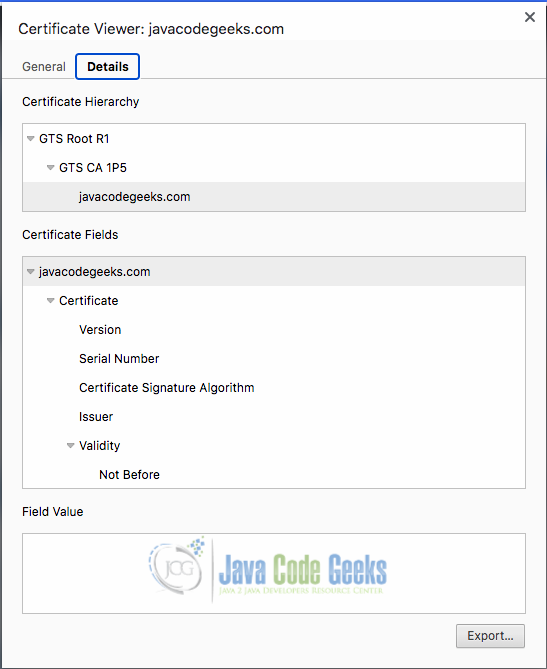
Verifying a certificate chain involves confirming the trustworthiness of each certificate in the chain, ultimately leading back to a root CA certificate that is trusted. Fig 1.3 shows the certificate hierarchy from the certificate acquired from the javacodegeeks website.
From the above image, we can deduce that:
- GTS Root R1 is the Root CA
- GTS CA 1P5 is an Intermediate CA
- javacodegeeks.com is the End Entity
3.2 Verifying CA Certificate
Verifying whether a certificate is a CA certificate involves examining specific attributes within the certificate. Java provides tools and libraries in the java.security package to work with certificates.
To check if a certificate is a CA certificate, we can use the KeyUsage extension and the BasicConstraints extension which is commonly found in CA certificates. Below is a simple Java program that verifies whether a given certificate is a Certificate Authority certificate or not.
public class CACertificateVerifier {
public static void main(String[] args) {
try {
// Load the certificate from a file
FileInputStream fis = new FileInputStream("path/to/certificate.cer");
CertificateFactory certificateFactory = CertificateFactory.getInstance("X.509");
X509Certificate certificate = (X509Certificate) certificateFactory.generateCertificate(fis);
// Check if the certificate is a CA certificate
boolean isCACertificate = isCACertificate(certificate);
// Display the result
if (isCACertificate) {
System.out.println("The certificate is a CA certificate.");
} else {
System.out.println("The certificate is not a CA certificate.");
}
} catch (Exception e) {
e.printStackTrace();
}
}
// Method to check if a certificate is a CA certificate
private static boolean isCACertificate(X509Certificate certificate) {
boolean isCACertificate = false;
// Check KeyUsage Extension
boolean[] keyUsage = certificate.getKeyUsage();
if (keyUsage != null && keyUsage.length > 5 && keyUsage[5]) {
// The 6th bit (index 5) corresponds to keyCertSign
isCACertificate = true;
}
// Check BasicConstraints Extension
if (certificate.getBasicConstraints() != -1) {
isCACertificate = true;
System.out.println(" IssuerDN is " + certificate.getIssuerDN());
}
return isCACertificate;
}
}
Here is an explanation of the code:
- First, we start by loading the certificate. The file path is specified in the
FileInputStream. This is where we provide the path to the certificate we want to examine. Note that you need to replace"path/to/certificate.cer"with the actual path to your certificate file. - The program then calls the
isCACertificatemethod, passing the loaded certificate as an argument. This method checks specific extensions within the certificate to determine if it’s a CA certificate. - The
isCACertificatemethod takes anX509Certificateas input and checks theKeyUsageextension and theBasicConstraintsextension.- KeyUsage Extension: It looks at the 6th bit of the
keyUsagearray, which corresponds to thekeyCertSignflag. If this flag is set, it indicates that the certificate is allowed to sign keys. - BasicConstraints Extension: It checks the
BasicConstraintsextension. If the result is not -1, it means the certificate is a CA certificate.
- KeyUsage Extension: It looks at the 6th bit of the
- Finally, based on the result obtained from the
isCACertificatemethod, the program prints whether the loaded certificate is a CA certificate or not. If it is, it also prints theIssuerDNfor additional context.
4. Conclusion
In this article, we explored the process of checking whether a certificate is self-signed or CA-signed using Java. By exploring the complexities of digital certificates and utilizing the security features offered by Java, we can implement reliable methods to determine the origin of certificates.
In conclusion, as Java developers, having the ability to perform a comprehensive Java check certificate sign operation is crucial for ensuring the authenticity and trustworthiness of certificates within our applications.
5. Download the Source Code
This was a tutorial on verifying whether a certificate is self-signed or signed by a certificate authority using Java (Java check certificate sign operation).
You can download the full source code of this example here: verifying whether a certificate is self-signed or signed by a certificate authority using Java(Java check certificate sign operation).